In October last year (2024), I started my internship at OPSWAT. By early 2025, I was assigned my first research project: finding vulnerabilities in one of the PLCs available in the company lab.
Together with my awesome boss and two fellow interns, we took on the challenge and chose the Modicon M241 PLC from Schneider Electric as our first stepping stone into the Operational Technology (OT) security field.

Why did we choose the Modicon M241 PLC? #
The answer is simple, just like the PLC itself.
The M241 uses the Modbus protocol, developed by Schneider Electric, which is one of the simplest protocols used in industrial controllers.
In addition, the PLC has a built-in web server with a variety of features and APIs—an area we were already familiar with. More importantly, it has a few past CVEs that we could use for reference and post-patch exploitation analysis.
The results #
We found 7 CVEs in the Modicon M241 PLC ᕙ( •̀ ᗜ •́ )ᕗ
These vulnerabilities also affect other PLC models.
Our credits: SEVD-2025-133-01, SEVD-2025-161-02
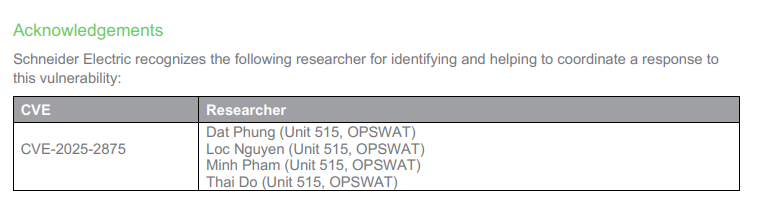
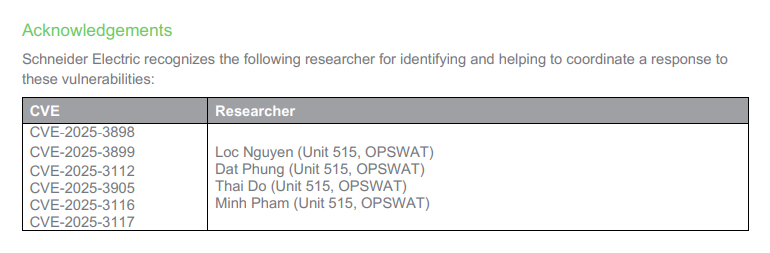
I also made it onto Schneider Electric’s Wall of Thanks ദ്ദി ˉ͈̀꒳ˉ͈́ )✧
For those who come after #
This project was a major milestone in my journey into OT security. Not only did I get hands-on experience with real-world machines and systems, but I also had the chance to contribute to public CVEs and work alongside a great team.
There’s still so much to explore in this field, and this is just the beginning.
See you in the next blog about the MELSEC FX5UJ PLC from Mitsubishi Electric which will be published soon ദ്ദി(˵ •̀ ᴗ - ˵ ) ✧

